Ransomware is a form of malware that prevents users and organizations from accessing files and data on their devices until they’ve paid a ransom. Once the ransom is paid, the cybercriminal promises to give the victim what they need to regain access to their devices. Oftentimes, the attacker will provide the victim with a decryption key depending on the type of ransomware attack.
It's important to note that cybercriminals cannot be trusted and do not always follow through with their promise to give back access. They may also strike again with a follow-on attack, if they know an organization is willing to pay a ransom.
Cybercriminals may also sell the sensitive data that was accessed on the dark web, even if the demanded ransom was paid. Ransomware attacks can result in substantial financial damage to businesses and have left many organizations from startups to major enterprises in dire conditions or shut them down altogether.
How Do Ransomware Attacks Work?
Ransomware can infect devices in several ways, depending on the threat actor behind the attack.
Phishing
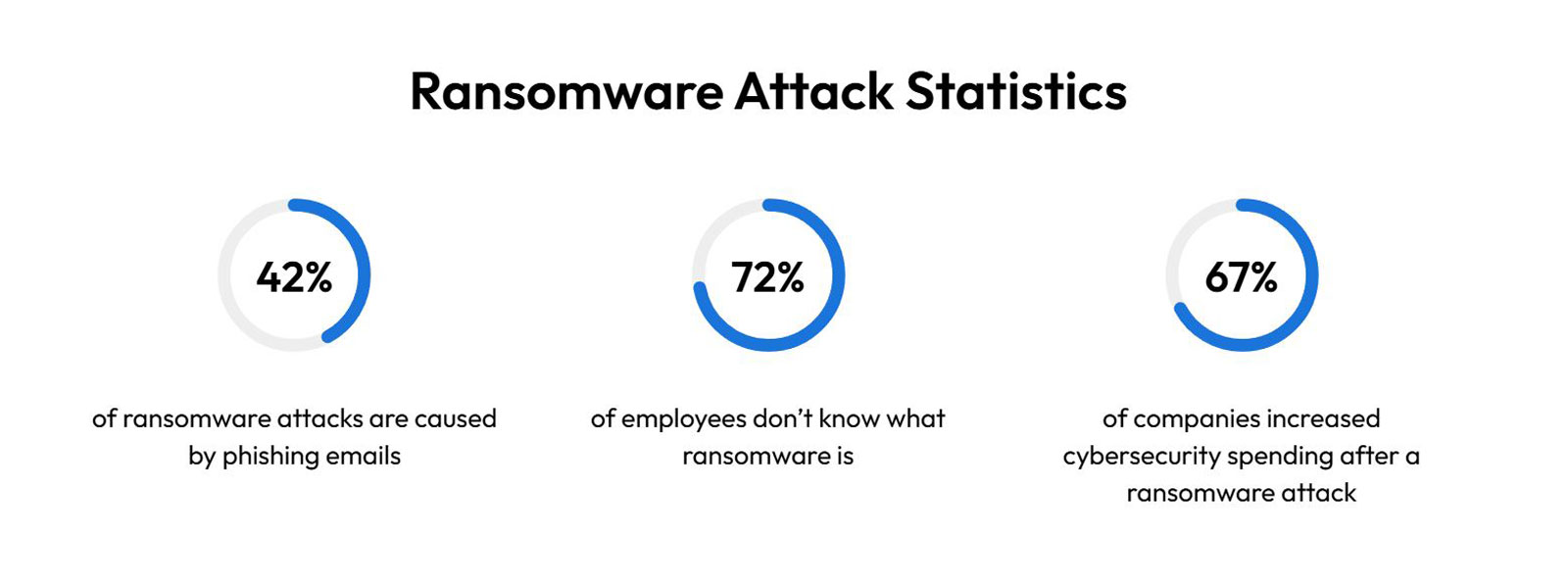
Phishing is a sophisticated social engineering attack that aims to persuade a victim into revealing sensitive information. Ransomware attacks commonly work by getting the targeted victim to unintentionally download malware through phishing emails. Without proper security tools and employee training on how to identify phishing emails, employees can disrupt their entire company with one click.
When an employee clicks on a link or attachment in a phishing email that contains ransomware, it slowly infects the employee’s device without them noticing. The ransomware can then spread through the connected network to infect the devices of other employees who are on the same network. As the ransomware spreads, files become encrypted – preventing anyone from accessing them until the ransom is paid.
Exploit Kits
Exploit kits are used by cybercriminals to attack vulnerabilities in systems in order to distribute malware. When victims go to malicious websites or click on malicious advertisements (malvertisements), targeted victims are directed to the exploit kit’s landing page. This is where the exploit kit determines vulnerabilities and then exploits them – allowing them to successfully infect the victim's devices with malware.
Once the victim’s device becomes infected, they’ll be demanded to pay a ransom before they are allowed to access their files and data.
Types of Ransomware Attacks
Crypto Ransomware
Crypto ransomware is one of the most common types of ransomware attacks. With this type of attack, the threat actor uses a program that encrypts the files on the victim's device. When encrypted, the contents of the files become scrambled – making them unreadable. The victim will receive an on-screen alert that says, in order to decrypt the files, they will need to obtain a decryption key from the attacker. An attacker won't provide the victim with a decryption key until they've paid the ransom.
It's worth noting that crypto ransomware differs from crypto malware, which is malicious software that allows threat actors to mine cryptocurrencies on a victim's device.
Locker Ransomware
Locker ransomware is another common type of ransomware attack. Using this type of attack, the malware will make the victim’s device inoperable. For example, when malware infects the victim’s device, the victim won’t be able to use their mouse or keyboard. The only thing the victim will be able to do on their device is pay the ransom, which will be the only thing displayed on their screen.
Instead of encrypting your files like crypto ransomware, locker ransomware will just lock you out and prevent you from using your device.