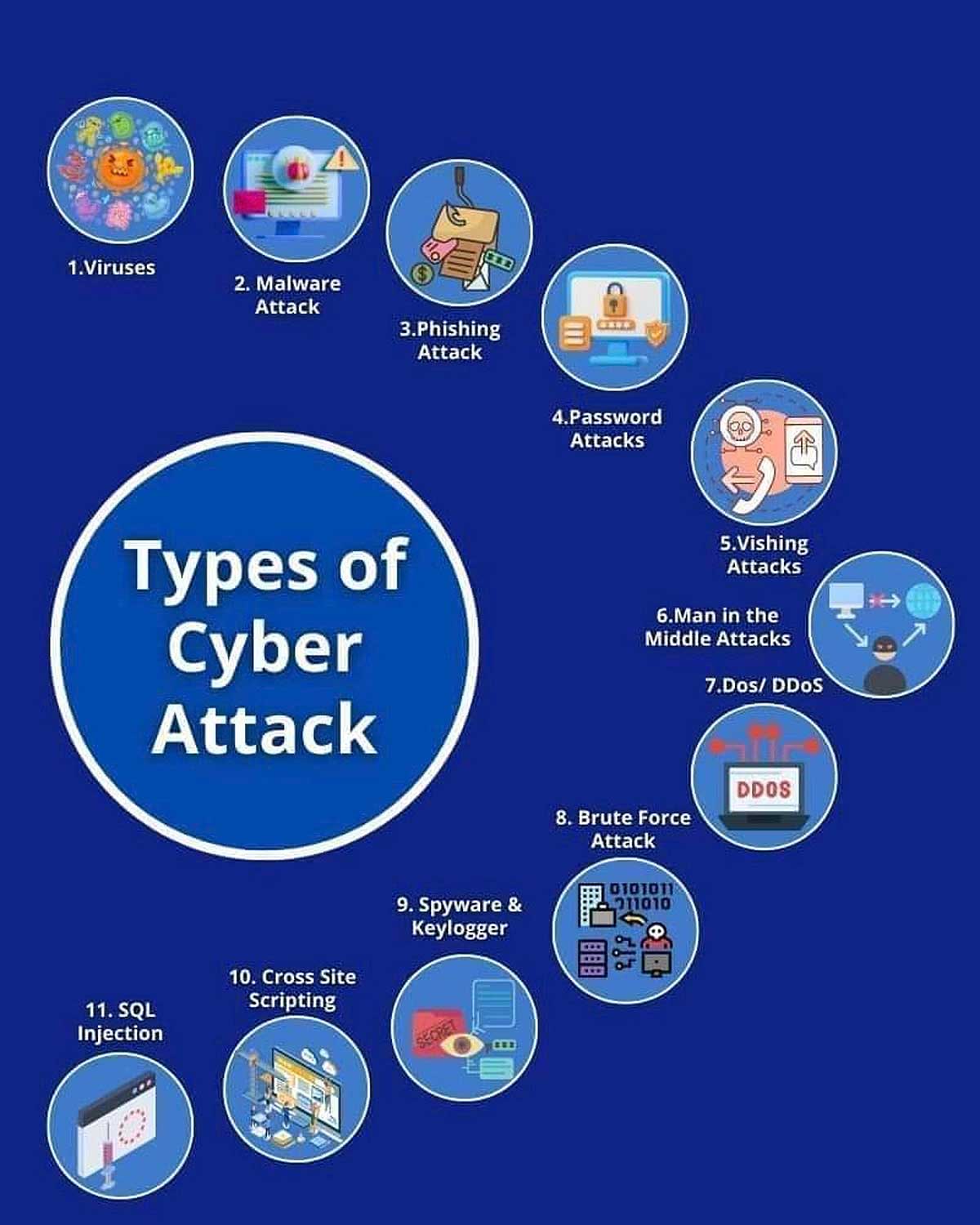
Here are some common types of Cyber Attacks
🦠 Malware: Software designed to harm or exploit systems, including viruses, worms, Trojans, and ransomware.
🎣 Phishing: Deceptive attempts to obtain sensitive information by posing as a trustworthy entity, often through emails or fake websites.
🚫 Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks: Overloading a system or network to make it unavailable to users.
🕵️ Man-in-the-Middle (MitM) attacks: Intercepting and possibly altering communication between two parties without their knowledge.
💉 SQL Injection: Exploiting vulnerabilities in a website's database by injecting malicious SQL code.
📜 Cross-Site Scripting (XSS): Injecting malicious scripts into webpages that are viewed by other users.
💻 Ransomware: Encrypting a user's files and demanding a ransom for their release.
🤖 Social Engineering: Manipulating individuals into divulging confidential information through psychological tactics.
🔓 Zero-Day Exploits: Targeting undiscovered vulnerabilities in software before a fix is available.
🔑 Password Attacks: Gaining unauthorized access by exploiting weak or stolen passwords, including brute force attacks and credential stuffing.
🌐 IoT-Based Attacks: Exploiting vulnerabilities in Internet of Things devices to gain unauthorized access or disrupt functionality.